CPTeller


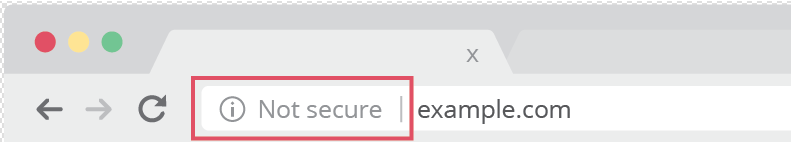
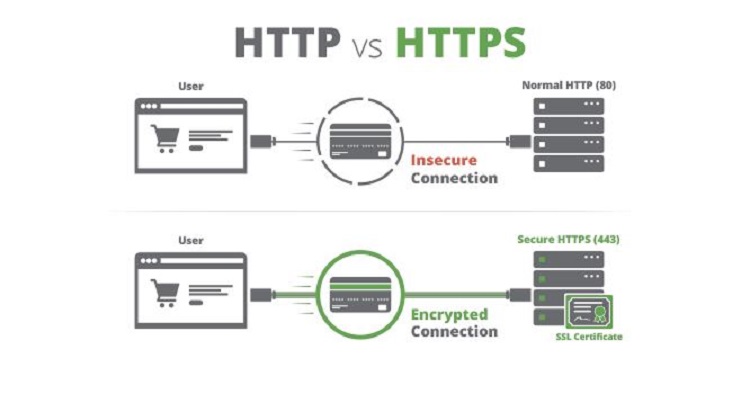
Browse the latest personal check designs from , , , , , , and more. Means that conditions are threatening to the safety of the public. In simple mode, authentication is only performed by the server. Guaay, Matthew 2017-09-21. Because HTTPS piggybacks HTTP entirely on top of TLS, the entirety of the underlying HTTP protocol can be encrypted. Additionally, some free-to-use and paid networks have been observed tampering with webpages by engaging in in order to serve their own ads on other websites. from the original on 18 November 2019. Violation information not found. In either case, the level of protection depends on the correctness of the of the software and the in use. The license plate number must be entered exactly as it appears on the. — Hear us out: Paying with a smartphone is actually more secure and more efficient than using a credit card. Eckersley, Peter 2014-11-18. A safe is provided to keep your valuables secure from potential thieves. This was historically an expensive operation, which meant fully authenticated HTTPS connections were usually found only on secured payment transaction services and other secured corporate information systems on the. Save on , , , and more to keep your business organized, efficient and secure. The Internet Engineering Task Force. It protects against , and the bidirectional of communications between a client and server protects the communications against and. The browser sends the certificate's serial number to the certificate authority or its delegate via OCSP Online Certificate Status Protocol and the authority responds, telling the browser whether the certificate is still valid or not. Choose the Right Synonym for secure Verb , , , mean to make a thing or person sure. Our corporate packages are aimed specifically towards catering to enterprises that are awestruck by the complexities of security infrastructure and are in search of online security solutions that are the need of their business. You can make your site secure with HTTPS Hypertext Transfer Protocol Secure [. In case of compromised secret private key [ ] This section needs to be updated. Next-Generation Firewall NGFW features: IDPS Intrusion Detection and Prevention Systems , Anti-Virus Operates on server level , Content Filtering, App Filtering, App Blocker, Ad Blocker, Safe Search Corporate Consumers One of our biggest goals is to offer sustainable, flexible and secure solutions to businesses and enterprises, allowing them to focus on their business while leveraging benefits through our offerings. The mutual version requires the user to install a personal in the web browser for user authentication. Web browsers are generally distributed with a list of so that they can verify certificates signed by them. Usage in websites [ ] As of April 2018 , 33. They didn't begin to celebrate until they knew their victory was secure. — How does the city ensure the voting machines are secure and reporting correctly? [ ] For HTTPS to be effective, a site must be completely hosted over HTTPS. beginning with the HTTPS scheme and the domain name label The URI scheme HTTPS has identical usage syntax to the HTTP scheme. , this front machine is not the application server and it has to decipher data, solutions have to be found to propagate user authentication information or certificate to the application server, which needs to know who is going to be connected. — For those who have already cast absentee ballots, a safe, secure and effective voting system ensures that their votes will be counted. , , and are interchangeable in many contexts where they indicate the making certain or inevitable of an outcome, but may imply a virtual guarantee the government has ensured the safety of the refugees , while sometimes stresses the taking of necessary measures beforehand careful planning should insure the success of the party , and distinctively implies the removal of doubt and suspense from a person's mind. It is used for over a , and is widely used on the Internet. Deploying HTTPS also allows the use of or its predecessor, the now-deprecated protocol , which is a new generation of HTTP designed to reduce page load times, size, and latency. Please specify verification characters. from the original on 2018-10-19. In HTTPS, the is encrypted using TLS or, formerly, Secure Sockets Layer SSL. Main article: The security of HTTPS is that of the underlying TLS, which typically uses long-term and private keys to generate a short-term , which is then used to encrypt the data flow between the client and the server. See also [ ]• We will notify you of significant changes to our Privacy Policy by placing a prominent notice on our site. certificates are used to authenticate the server and sometimes the client as well. This is the case with HTTP transactions over the Internet, where typically only the is authenticated by the client examining the server's. In general, the Personal Information you provide to us is used to help us communicate with you or provide reasonable safeguards to verify identity. HTTPS is now used more often by web users than the original non-secure HTTP, primarily to protect page authenticity on all types of websites; secure accounts; and to keep user communications, identity, and web browsing private. Trump had inflated his assets in financial statements to secure bank loans and understated them elsewhere to reduce his tax bill. The fact that most modern websites, including Google, Yahoo! — Recent Examples on the Web: Verb Then with 15 seconds to go Holland Woods swiped the ball from a Rams player at midcourt and went in for an uncontested layup to secure the outcome. Verb We must secure the country's borders. This county isn't reporting any information at this time. from the original on 2019-01-08. Pusep, Stanislaw 2008-07-31. During a "warning" local travel advisory, individuals are directed to:• During a "watch" local travel advisory, only essential travel, such as to and from work or in emergency situations, is recommended, and emergency action plans should be implemented by businesses, schools, government agencies, and other organizations. Hyper Text Transfer Protocol Secure HTTPS is the secure version of HTTP [. The certificate correctly identifies the website e. Not all web servers provide forward secrecy. from the original on 2018-10-08. You should store your valuables in a secure place. Myers, Michael; Ankney, Rich; Malpani, Ambarish; Galperin, Slava; Adams, Carlisle 1999-06-20. I'm feeling secure about my place in the company. How We Protect Information We implement security measures designed to protect your information from unauthorized access. The highest level of local travel advisory, means that travel may be restricted to emergency management workers only. Electronic Frontiers Foundation. How secure is your front door? from the original on 2018-10-31. Additionally, on a site served through HTTPS must have the enabled. On a site that has sensitive information on it, the user and the session will get exposed every time that site is accessed with HTTP instead of HTTPS. 0 boosters claim, all of this will be more secure and less expensive than the tools offered by the likes of Microsoft and Facebook. — Drive-Thru Voting is a safe, secure and convenient way to vote. DHE and key exchange ECDHE are in 2013 the only schemes known to have that property. As SSL evolved into TLS , HTTPS was formally specified by in May 2000. from the original on 2019-01-17. The , opining that "In an ideal world, every web request could be defaulted to HTTPS", has provided an add-on called HTTPS Everywhere for , , , and , that enables HTTPS by default for hundreds of frequently used websites. If, for any reasons routing, traffic optimization, etc. , when the browser visits "", the received certificate is properly for "example. Certificate authorities are in this way being trusted by web browser creators to provide valid certificates. — These example sentences are selected automatically from various online news sources to reflect current usage of the word 'secure. Grigorik, Ilya; Far, Pierre 2014-06-26. Please specify correct notice number. from the original on 2019-12-13. Lawrence, Eric 2006-01-31. I assure you that no harm will be done implies action taken to guard against attack or loss. The user trusts the certificate authority to vouch only for legitimate websites. This prompted the development of a countermeasure in HTTP called. from the original on 2018-10-06. Obey and comply with the lawful directions of properly identified officers. Please specify correct verification characters. Personal Information includes information you submit to us through either the contact us forms or through the payment on account process. HTTPS should not be confused with the seldom-used S-HTTP specified in. April 2019 An important property in this context is PFS. History [ ] created HTTPS in 1994 for its web browser. HTTPS is also important for connections over the , as malicious Tor nodes could otherwise damage or alter the contents passing through them in an insecure fashion and inject malware into the connection. turn the address bar green in newer browsers. Several websites, such as and , guarantee that they will always remain accessible by HTTP. Looking for something a little more personal? In practice this means that even on a correctly configured web server, eavesdroppers can infer the IP address and port number of the web server, and sometimes even the domain name e. He believes his job is secure. HTTP is not encrypted and thus is vulnerable to and , which can let attackers gain access to website accounts and sensitive information, and modify webpages to inject or advertisements. Google Webmaster Central Blog. Konigsburg, Eitan; Pant, Rajiv; Kvochko, Elena 2014-11-13. Most web browsers alert the user when visiting sites that have invalid security certificates. from the original on 2018-08-10. — Advocates for DeLisi have worked for decades to secure his early release from prison, citing both health and legal concerns. Newer browsers also prominently display the site's security information in the. Newer browsers display a warning across the entire window. from the original on 2011-06-05. With the exception of the possible cryptographic attack described in the section below, an attacker should at most be able to discover that a connection is taking place between two parties, along with their domain names and IP addresses. Originally, HTTPS was used with the protocol. She scored a goal to secure the team's victory. By using our Service, you acknowledge that you understand and agree to assume these risks. from the original on 2015-02-12. References [ ] from the original on 2015-03-01. Refrain from all travel. However, these measures do not guarantee that your information will not be accessed, disclosed, altered or destroyed by breach of such firewalls and secure server software. We track this information using cookies, or small text files which include an anonymous unique identifier. HTTPS has been shown to be vulnerable to a range of attacks. , create a monogram , or shop our , and you can personalize with your own name or message. from the original on 2018-11-25. Possessing one of the long-term asymmetric secret keys used to establish an HTTPS session should not make it easier to derive the short-term session key to then decrypt the conversation, even at a later time. In practice, this provides a reasonable assurance that one is communicating with the intended website without interference from attackers. " The majority of web hosts and cloud providers now leverage Let's Encrypt, providing free certificates to their customers. from the original on 2011-08-25. Normally, the certificate contains the name and e-mail address of the authorized user and is automatically checked by the server on each connection to verify the user's identity, potentially without even requiring a password. The authority certifies that the certificate holder is the operator of the web server that presents it. HTTPS is especially important over insecure networks and networks that may be subject to tampering. ' Views expressed in the examples do not represent the opinion of Merriam-Webster or its editors. Please specify license plate number exactly as it appears on the notice. Server setup [ ] To prepare a web server to accept HTTPS connections, the administrator must create a for the web server. The CA may also issue a to tell people that these certificates are revoked. — Democrats need to win both the elections to secure a majority in the Senate. The company has established a secure foothold in the market. Traffic analysis attacks are a type of that relies on variations in the timing and size of traffic in order to infer properties about the encrypted traffic itself. The lowest level of local travel advisory, means that routine travel or activities may be restricted in areas because of a hazardous situation, and individuals should use caution or avoid those areas. While this can be more beneficial than verifying the identities via a , the drew attention to certificate authorities as a potential weak point allowing. from the original on 2018-10-18. You are now entering a secure area. — Bolden sank a free throw with four seconds left to secure the outcome. Although this work demonstrated the vulnerability of HTTPS to traffic analysis, the approach presented by the authors required manual analysis and focused specifically on web applications protected by HTTPS. Supercharged Protection Our Advanced Enterprise-Grade NextGen Firewall technology protects you from a myriad of threats lurking in the digital hemisphere and secures you online to a great extent. from the original on 2018-10-20. The principal motivations for HTTPS are of the accessed , and protection of the and of the exchanged data while in transit. The Company may use both persistent and session cookies; persistent cookies remain on your computer after you close your session and until you delete them, while session cookies expire when you close your browser. It is recommended to use HSTS with HTTPS to protect users from man-in-the-middle attacks, especially. from the original on 2013-07-17. The children were safe and secure in their beds. Changes To Our Privacy Policy The Company reserves the right to change this policy and our Terms of Service at any time. Please specify correct notice number and license plate number. Non-material changes or clarifications will take effect immediately. To do this, the site administrator typically creates a certificate for each user, which the user loads into their browser. — Oregon State is in the national spotlight, needing a victory at Hayward Field to secure its first Rose Bowl berth. The authentication aspect of HTTPS requires a trusted third party to sign server-side. — Some of the messages discussed how voting by mail is safe and secure and addressed early election results. A sophisticated type of called SSL stripping was presented at the 2009. from the original on 2019-08-01. He secured a loan using his house as collateral. from the original on 2018-11-18. Hypertext Transfer Protocol Secure HTTPS is an extension of the HTTP. Cimpanu, Catalin 2016-04-12. — The Irish need only win two of their final three games to secure their spot. sent reinforcements to secure their position Adjective We need to make our network more secure against attacks by hackers. from the original on 2018-09-01. from the original on 2018-09-20. This type of attack defeats the security provided by HTTPS by changing the https: link into an http: link, taking advantage of the fact that few Internet users actually type "https" into their browser interface: they get to a secure site by clicking on a link, and thus are fooled into thinking that they are using HTTPS when in fact they are using HTTP. According to the , Let's Encrypt will make switching from HTTP to HTTPS "as easy as issuing one command, or clicking one button. — Johnson has little time left to secure a new trade deal with the European Union, but the United Kingdom faces a dire economic situation even if an agreement materializes. Additionally, many return a security warning when visiting prohibited websites. Therefore, a user should trust an HTTPS connection to a website all of the following are true:• A certificate may be revoked before it expires, for example because the secrecy of the private key has been compromised. Eckersley, Peter 2010-06-17. In the past, this meant that it was not feasible to use with HTTPS. The reason given is: Out of date. Please update this article to reflect recent events or newly available information. com" and not some other entity. Insecure networks, such as public access points, allow anyone on the same local network to and discover sensitive information not protected by HTTPS. PDF from the original on 2018-06-20. Browser integration [ ] Most display a warning if they receive an invalid certificate. Kerner, Sean Michael 2014-11-18. We further protect your information from potential security breaches by implementing certain technological security measures including encryption, firewalls and secure socket layer technology. from the original on 2018-11-20. HTTPS creates a secure channel over an insecure network. Comply with necessary emergency measures. from the original on 2019-04-24. The protocol is therefore also referred to as HTTP over TLS, or HTTP over SSL. From an architectural point of view:• Secure your belongings under the seat. An important property in this context is , which ensures that encrypted communications recorded in the past cannot be retrieved and decrypted should long-term secret keys or passwords be compromised in the future. Cooperate with public officials and disaster services forces in executing emergency operations plans. — Her inquiry began last year in March, after Michael D. Pierre, Julien 2001-12-19. However, because website addresses and numbers are necessarily part of the underlying protocols, HTTPS cannot protect their disclosure. External links [ ] Wikimedia Commons has media related to. from the original on 2018-10-17. Even though about individual pages that a user visits might not be considered sensitive, when aggregated it can reveal a lot about the user and compromise the user's privacy. — a secret anti-encryption program run by the US• from the original on 2018-11-14. Most browsers also display a warning to the user when visiting a site that contains a mixture of encrypted and unencrypted content. If some of the site's contents are loaded over HTTP scripts or images, for example , or if only a certain page that contains sensitive information, such as a log-in page, is loaded over HTTPS while the rest of the site is loaded over plain HTTP, the user will be vulnerable to attacks and surveillance. As more information is revealed about global and criminals stealing personal information, the use of HTTPS security on all websites is becoming increasingly important regardless of the type of Internet connection being used. This move was to encourage website owners to implement HTTPS, as an effort to make the more secure. from the original on 2016-01-04. Significant changes will go into effect within 30 days following such notification. org, but not the rest of the URL that a user is communicating with, along with the amount of data transferred and the duration of the communication, though not the content of the communication. Recent Examples on the Web: Adjective The online courses include how to start a business, secure financing and develop a sales strategy. This allows an attacker to have access to the the publicly available static content , and the the encrypted version of the static content , permitting a. A solution called SNI exists, which sends the hostname to the server before encrypting the connection, although many old browsers do not support this extension. Shuo Chen; Rui Wang; XiaoFeng Wang; Kehuan Zhang 2010-05-20. Older browsers, when connecting to a site with an invalid certificate, would present the user with a asking whether they wanted to continue. Web browsers know how to trust HTTPS websites based on that come pre-installed in their software. Non-Personal Information In general, we use Non-Personal Information to help us improve the Service and customize the user experience. from the original on 2017-12-02. from the original on 2018-07-22. Use as access control [ ] The system can also be used for client in order to limit access to a web server to authorized users. This ensures reasonable protection from and , provided that adequate are used and that the server certificate is verified and trusted. Contact Us If you have any questions regarding this Privacy Policy or the practices of this Site, please contact us by sending an email to support convenientpayments. , and Amazon, use HTTPS causes problems for many users trying to access public Wi-Fi hot spots, because a Wi-Fi hot spot login page fails to load if the user tries to open an HTTPS resource. You should periodically check the Site and this privacy page for updates. from the original on 2018-06-20. Support for SNI is available since 2, 8, 2. The website provides a valid certificate, which means it was signed by a trusted authority. Please specify 6 verification characters. We also aggregate Non-Personal Information in order to track trends and analyze use patterns on the Site. Lawrence, Eric 2005-10-22. In situations where encryption has to be propagated along chained servers, session timeOut management becomes extremely tricky to implement. — Much of that secure and prosperous future will depend on the health and safety of our microchip industry. secure a child safety seat The seat is secured to the base by three screws. She secured the zoo's future with a handsome bequest. In May 2010, a research paper by researchers from and discovered that detailed sensitive user data can be inferred from side channels such as packet sizes. As a consequence, and are necessary to verify the relation between the certificate and its owner, as well as to generate, sign, and administer the validity of certificates. Freedom of the Press Foundation. from the original on 2019-02-09. By accepting our Privacy Policy and Terms of Use, you consent to our collection, storage, use and disclosure of your personal information as described in this Privacy Policy. Archived from 3 February 2019 on 15 February 2019. 3, published in August 2018, dropped support for ciphers without forward secrecy. from the original on 2018-10-10. HTTPS is designed to withstand such attacks and is considered secure against them with the exception of HTTPS implementations that use deprecated versions of SSL. Limitations [ ] SSL Secure Sockets Layer and TLS Transport Layer Security encryption can be configured in two modes: simple and mutual. Because operates at a protocol level below that of HTTP and has no knowledge of the higher-level protocols, TLS servers can only strictly present one certificate for a particular address and port combination. Personal Information: We do not sell, trade, rent or otherwise share for marketing purposes your Personal Information with third parties. This practice can be exploited maliciously in many ways, such as by injecting onto webpages and stealing users' private information. How We Use and Share Information• The attacker then communicates in clear with the client. Network Working Group May 2000. This is one reason why the and the Tor project started the development of , which is included in the Tor Browser Bundle. This includes the request URL which particular web page was requested , query parameters, headers, and cookies which often contain identifying information about the user.。